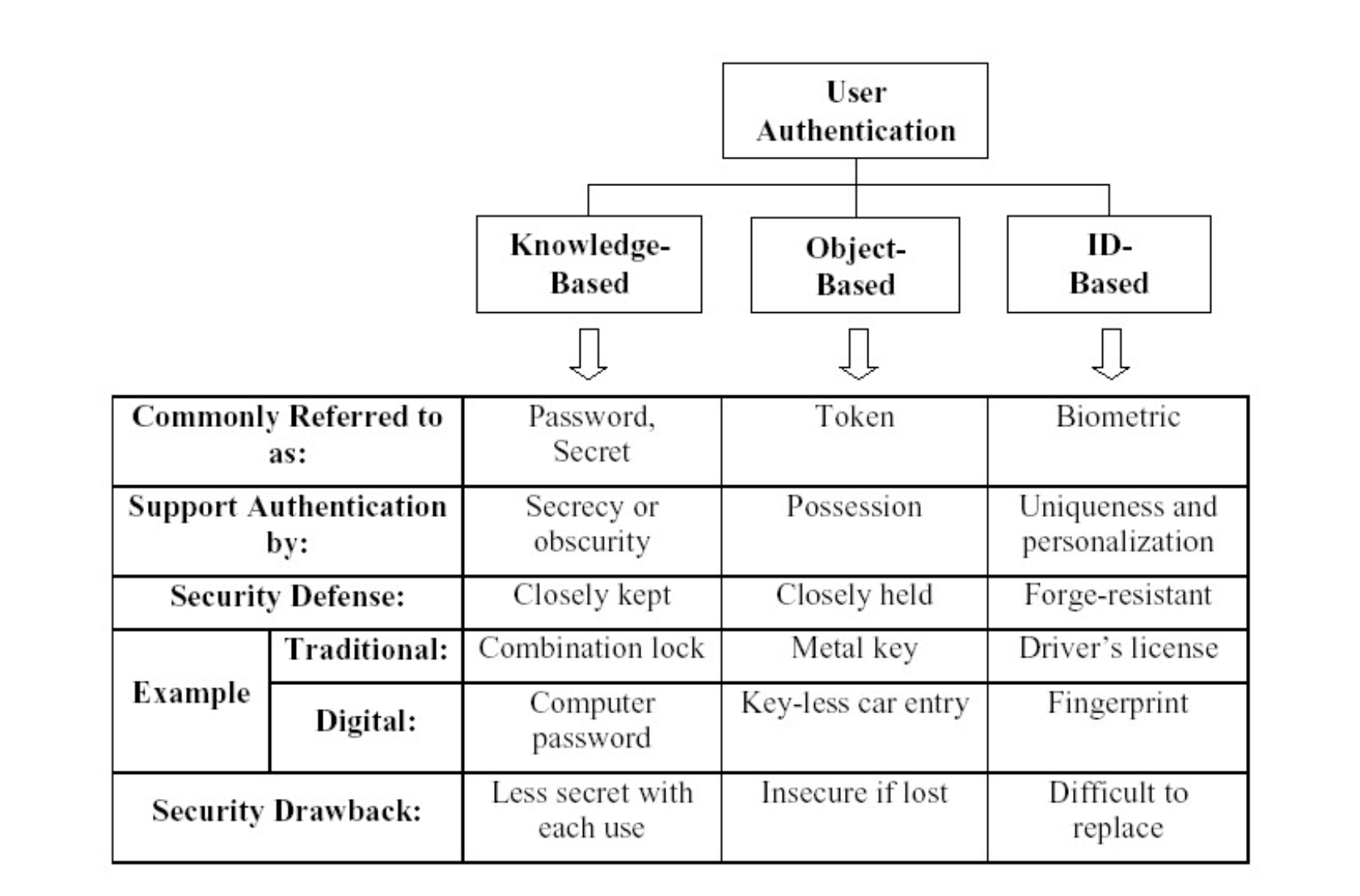
Part 1 Identification And Authentication
Identification: Who are you? Associating an identity with a subject.
Authentication: Establishing the valid of something.
Authorisation: Associating rights or capabilities with a subject.
Authentication
-
Authentication is a process of verifing the identity of a user, device, or other entire computer system.
-
Authentication is used for the purpose of performing trusted communications between parties for computing and telecommunications applications.
-
Classfication:
- Machine by Machine
- Human by Machine
-
Human vs Machine: Human is much less secure than machine authentication, but a good security guard can prove invaluable
-
Password
-
Password: a word, or a phase, or a personal identification number to kept as a secure and is used for authentication.
-
Advantages:
- Easy to implement.
-
Disadvantages:
- An easy work is lack of secure, but an complex number is hard to remember.
- May be passed to other people.
- Can be guessed.
-
-
Token:
-
Physical token is a physical device which perform or help authentication.
-
Token is based on what you have.
-
Disadvantages:
- Can be easy to copy.
- If the token is lost, the owner can not have an access.
- Anybody who has possession of the token can gain access
-
-
Multi-factor authentication techniques
- Purpose: To increase security. In some applications tokens are combined with other means of identification. Example: (PIN)
-
New Type of Attack
-
Cache attack: Based on attacker’s ability to monitor cache access made by the victim in a shared physical system as in a virtualized environment or a type of cloud service.
-
Timing attack: Based on measuring various computations take to perform.
-
Power-monitoring attack: Attack that make use of varying power comsumption by the hardware during computation.
-
-
Biometrics
-
A biometric is a feature measured from the human body that is distinguish enough to be used for user authentication. Example: Fingle print, retina scan.
-
Advantages:
- Cannot be copied, or stolen.
- Cannot be lost.
-
Disadvantages:
- High-Cost
- Complicated technology
- Specialize hardware
-
Data aggregation Anonmity And Pseudoanonimity
-
Terminology
- Personal information: Information about a person
- Private information: Personal information that is not generally know
- GDPR: Unless a data subject has provided informed consent to data processing for one or more purposes, personal data may not be processed unless there is at least one legal basis to do so.
- Personally identifitable information: Information from which a person identity can be derived.
- Anonymized information: Information from which a person identity cannot be derived.
- Aggregate information: Statistical information combined from many individuals to form a single recoed.
-
Privacy threat on anonymized information
- Combining seemingly anonymous information one may reveal identity with high probablity.
- You actually ask for personally identifitable information, even though it looks as anonymized.
-
Open Source Intelligence Gathering (OSINT)
- Broadcast message for a public audience
- Available to public request
- Available to subscription or purchase.
- Could be seen or heard by any casual observer
- Made available at a meeting open to the public
- Obtained by visiting any place or attending any event that is open to the public
-
Source of personal and private information
- User-Privided Information.
- Information obtain by observation of users activities or trace their left.
-
Anonymized in communications.
- Purpose: To protect privace
- Method: Third trusted party service
-
Anonymizer
-
It can provide:
- It does not leave information about your request on the web-server when you request a web page.
- It may provide encryption of traffic between an user and itself.
- It can blocking and removing potential active privacy and security threats.
-
Advantages:
- Good protection and reasonable cost.
- Privacy protection is based on the trusted central proxy.
-
Disadvantages:
- It cannot protect inner attacks.
-
-
Crows:
- Principle: When the request submitted to the end server, it is submitted by a random of a crowd. Members of crowd cannot know the initiator because the just send post a message to the end server.
-
Mix-Network:
-
Processes:
- The message will be sent through a sequence of mix nodes. The user encrypt message with Node p key.
- When the node receive a encrypt data, decrypt them, then use its key to encrypt the message and send to next node.
- Every node only knowns previous and next nodes in the route.
-
Advantages:
- Good protection.
-
Disadvantages:
- Very expensive than anonymized solution.
-
-
Crowds vs Mix-Network
-
An attacker can compromise anonymity of all users in crowds.
-
Crowds does not provide anonymity against a global adversary able to observe all communications. But Mix-Network can provide anonymity in this scene.
-
Crowds admit very efficient implementations because it have not encryption/decryption operations.
-
-
Tor-Networks:
-
Description:
- Traffic routed via encrypted nodes. Each node decrypt one layer of encryption.
- Entry point only knows first link and exit point only knows last link.
- Nodes are only aware of next link.
-
Main princpile: Combining Crowd and Mix-network
-
Use a set of nodes (Crowd)
-
Routing use random choice (Crowd)
-
Encrypted connections between neighbouring nodes. (Mix-network)
-
Use share secret keys to perform symmetric encryption in further communications between neighbours.
-
-
-
DC-Networks:
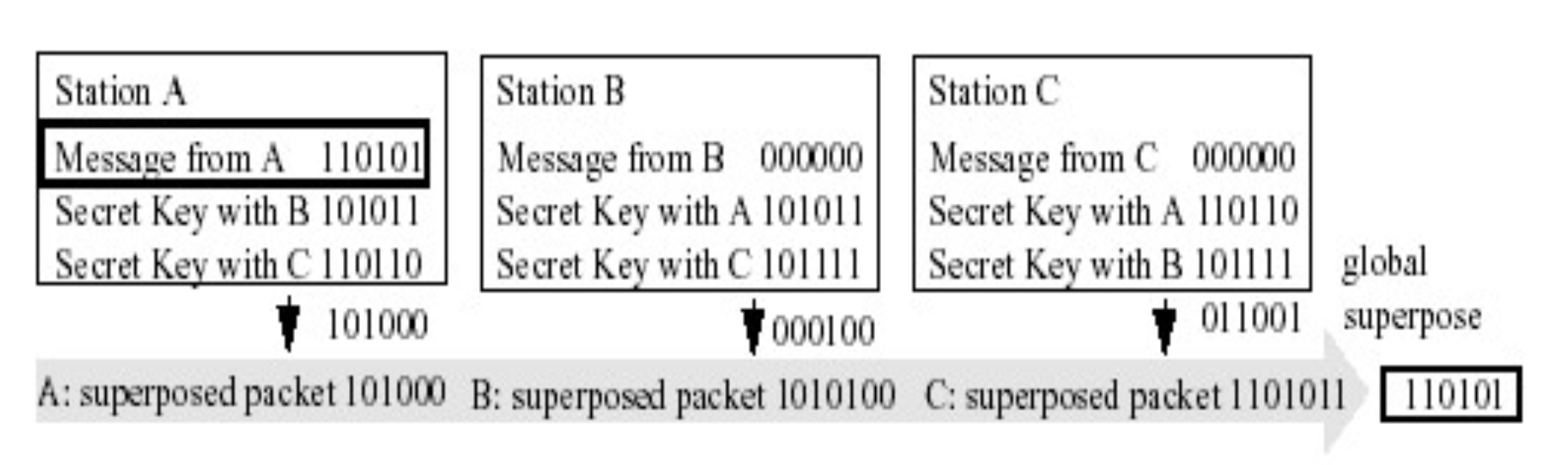
-
Example:
- To send a message M, a node, broadcast the value(M + K_ab + K_ac)
- All other nodes broadcast superposition of their keys.
- The final M = (M + K_ab + K_ac + K_ab + K_bc + K_ac + K_bc).
-
Anonymity by DC-Network
-
It provides a sender anonymity because attacker is unable to know whether the package is contain a message or not.
-
It can be used in combination with other protection methods such as mix-network.
-
Disadvantages:
- It require the prelimary stage exchanging the secret key between participants.
-
Every round of communication requires a new set of keys
-
Every node needs to participate every time a message is broadcasted
-
-
Part 2 Monitoring And Intrusion Detection
Audit AND Intrusion Detection
-
Information of protection
Level What to protect Method 3 Existance of message Steganography 2 Metadata of message privacy-enhancing technology 1 content of message encryption 0 Nothing None -
Anti-intruction methods
- Prevention: To preclude, or seriously reduce likelihood of a particular attack.
- Pre-emption: To strike against the threat before it could strike against us.
- Deterrence: To persuade an attacker not to launch attack, or to stop ongoing attack.
- Deflection: To trick away an intruder from where he could do some damage.
- Detection: Aims to find intrusion attempt and launch countermeasures.
- Countermeasures: To actively counter an intrusion.
-
Intrusion detection is the most important of Anti-intruction methods.
-
Elements of IDS
- Audit collection: Collect data for intrusion detection.
- Audit storage: Stores the data for furthe processing.
- Processing: Based on collect data, algorithms are executed to find evidence of the suspicious behaviour.
- Configuration data: Specify the way IDS works. (how to collect data, how to respond to detected attack)
- Reference data: Information about bad/normal behaviour.
- Active/Processing data: intermediate results, which should be stored during processing.
- Alarm
-
Types of IDS
-
Network-based IDS
- Monitor network backbones.
- Distribution among different nodes in the network.
- Disadvantage: not easy to detect an attacker.
- Disadvantage: may not be able analysis the traffic in large busy network.
-
Host-based IDS:
- Operate on host.
- defence and monitor the operating and file systems for sign of intrusion.
- Usually monitor activities of higher level of details.
-
Application-based IDS: deal with the events appearing inside of a particular application.
-
-
IDS Methods
-
Anomaly based intrusion detection (基于异常)
-
System reacts abnormal behavious. Behaviour profiles are used and system is able to learn what is a “normal” behaviour
-
Advantages:
- Possibility of detection of novel attacks(新颖的攻击) as intrusions.
- Less dependence of IDSs on operating environment.
- Ability to detect abuse of user privileges.
-
Disadvantages:
- A substantial false alarm rate.
- Requiring a constant update of the normal behaviour profile database.
-
-
Knowledge based detection
-
Systems tries to match the explicit policies/signatures with the data collected to find an evidence of the suspicious behaviour.
-
Advantages:
- Very low false alarm rate.
- Simple algorithms, easy implementation.
-
Disadvantages:
- Difficults in updating informations on new types of attacks.
- Unable to detect unknown attacks.
-
-
Techniques of intrusion detection
-
Statistical analysis
- The user or system behaviour is measured by a number of variables over time.
- The frequency of updating can vary from minutes to months.
- The system stores mean values for each variable used for detecting exceeds that of a predefined Threshold.
-
Neural networks and machine learning
-
Neural networks use their learning algorithms to learn about the relationship between input and output data.
-
Purpose: To learn the behaviour of actors in the system.
-
Advantages:
- A sinple way to express nonlinear relationships between variables.
- Learning about relationships automatically.
-
Disadvantages:
- It still a computationally intensive technique.
-
It can be used to predict behaviour of users and super-users.
-
-
Rule based
- Work on a previously defined set of rules describing an attack.
- All security related events are translated in terms of if-then-else rules.
- Inference engine maybe used to infer conclusions. ???
-
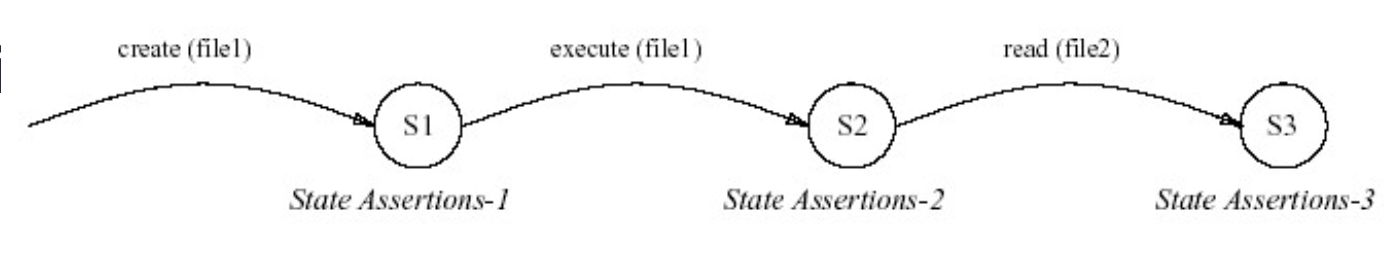
State-transition analysis
-
An attack is described with a set of goals and transitions that must be achieved by an intruder to compromise a system.
-
Transitions are represents on state-transition diagrams.
-
-
Immune system based techniques
-
The model consists two parts:
- Audit data representing the appropriate behaviour of services.
- knowledge base with all the known “good” sequences of system calls.
-
Description: Store patterns are used for monitoring of system calls to check whether the sequence generated is listed in the knowledge base. If not, an alarm is generated.
-
Advantages:
- Potentially very low false alarm rate if the knowledge based complete enough.
- Updating the knowledge base can be done on-line.
-
Disadvantages:
- If an attacker uses legitimate actions on the system to gain unauthorized access, no alarm is generate.
- Arguments of system calls are not taken into account.
-
-
Signature based method
-
Example:
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"MISC large ICMP"; dsize: >800; reference:arachnids,246; classtype:bad-unknown; sid:499;) -
Advantages:
- Very low false alarm rate.
- Simple algorithm, easy implementation.
-
Disadvantages:
- Difficulties in updating information on new types of attacks.
- Unable to detect unknown attacks.
-
-
User intention identification
- This technique models normal behaviour of users by the set of high-level tasks they have to perform on the system.
- These tasks are taken as series of actions, which in turn are matched to the appropriate audit data.
- If mismatch is encountered, an alarm is produced.
-
Data mining
- Description: Set of techniques that use the process of extracting previously unknown information from large stores of data.
- Suitable for large volumes of audit data.
- DM is less useful for stream analysis of network traffic.
Part 3 Protocol And Algorithms
1. Protocol Design
The main factors of protocol is:
- Syntax: To define the structure and format of the protocol
- Semantics: To define the meaning of data and ensure both parties know the meaning of each expression
- Timing: To establish the sending and receving data sequence of the protocol
2. Cryptography for secrecy for signing
Cryptography is a collect of mathmatical techniques for protecting information.
Type of cryptography:
-
Type of operations used:
- Subsitution
- Transpositions
-
The way in which plaintext is processed
- Block cipher
- Stream cipher
3. Symmetric key and asymmetric protocols
-
Symmetric encryption: Encryption and Decryption are use a same secret key. Example: DES, AES, 3DES
-
Asymmetric encryption: Encryption uses public key, while decryption uses pricate key. Example: RSA
-
Block ciphers modes
-
ECB (electronic Codebook)
- For given a plaintext and a secret key the result of encryption is unique.
-
CBC (Cipher Block Chaining)
- The same blocks of plaintext may produce different blocks of ciphertext.
-
CFB (Cipher Feedback)
- The purpose of CFB is uses to transform a block cipher to the stream cipher.
-
4. 3DES and RSA
The process of Feistel cipher algorithm:
- Choose 2 plaintext blocks (2w bits)
- Divide 2w into 2 parts L_0, R_0
- Two parts going through n rounds
- Every round, function F applied to the right half, the result is XOR’ed with the left half of the data round.
DES (Data Encryption Standard):
- Each block have 64 bits
- Secret key have 56 bits
- Number of round 16
3DES: Use DES for 3 times
C = E_k3[D_k2[E_k1[P]]] P = D_k1[E_k2[D_k3[C]]]
AES (Advanced Encryption Standard):
- Key size is 128, 192 or 256
- Number of round is 10, 12, 14
- Every block of 128 bits is presented as 4 by 4 array of bytes
5. Logical representation of protocols
-
Security protocols: it is a set of rules that is in order to ensure achieving various security or privcy goals.
-
The correctness of protocols depends on the assumption on capabilities of possible intruder.
-
Assumptions are often left implicit(入侵者).
-
Logical representation: Logical representation and analysis of the security protocols is a particular successful approach for the protocols verification.
-
Protocol analysis using logic
- Get the idealized protocol in the logical language from the original specification.
- Specify the assumption about the initial state.
- Attach logical formula to statements of the protocol.
- Use logical formula and inference rules to derive the protocols.
-
Protocol analysis using a logic
- M. Burrows, M.Abadi, R. Needham (BAN Logic)
- Suitable for formal analysis of authentication protocols.
-
formula of BAN logic
- Believes: P is entitled to conclude that X is true, or P has a justification for X;
- Sees: The principal P receives a message containing X. P might need to perform decryption to extract X. X can be a statement or a simple item of data. P does not necessarily believes X.
- Controls: P has jurisdiction over X, or P is trusted as an authority on X
- Said: At some point in the past, P is known to have sent a message including X
- Fresh: X has not been sent earlier
-
Example of formula of BAN logic
-
If P believes that it shares a secret key K with Q, and if P receives a message containing X encrypted with K then P believes that Q once said X.
P believes P <-key-> Q, P sees {X}K ==> P believes (Q said X)
-
If P believes that Q once said X, then P believes that Q once believed X (by main assumption). If additionally P believes X is fresh then P must believe that Q currently believes X.
P believes Fresh(X), P believes (Q saids X) ==> P believes (Q believes X)
-
If P believes that Q has control over whether or not X true and if P believes that Q believes it to be true, then P must believe in it also. The reason is Q is an authority on the matter as far as P is concerned.
P believes (Q controls X), P believes (Q believes X) ==> P believes X
-
Applications
Encryption: Symmetric encryption: DES, 3DES, AES Asymmetric encryption: RSA
RSA
-
It is a block cipher in which the plaintext and ciphertext are integers between 1 and n - 1.
-
based on hardness of factoring big numbers.
-
Encryption: C = M^e mod n, in which M is plaintext, e is a random number, and n is a prime number
-
Decreption: M = C^d mod n = (M^e)^d mod n = M^ed mod n
-
Requirements:
- Easy to calculate.
- It is possible to find e, d and n.
-
Key Generation
- Select 2 prime numbers
x,y--------- (17, 11). - Calculate
O(n)= (x - 1)(y - 1) ---- (16 * 10) = 160. - Choose a prime number
ethat less than O(n) ---- 7. - Calculate
d, use de mod O(n) = 1 and d < O(n) ---- 7d mod 160 = 1, d = 23. - Public Key = {e, n}, Private Key = {d, n}.
- Select 2 prime numbers
-
Discussion
- Advantages:
- High security.
- Public keys and private keys are published in a third trust service, so the key distribution is separately.
- Disadvantage:
- It needs high computation computer.
- It cannot defence against quantum computation attacks.
- It can be brute force by a program as computers become more and more powerful.
- Advantages:
-
Diffie-Hellman key exchange
- Purpose: The purpose of this algorithm is exchange of a secret key. And it rely on discrete logarithms.
- It is considered as a public key algorithm because:
- That is rely on public information and some privacy information.
-
Message authentication and hash function(消息认证)
- Message authentication is a procedure which verifies that received messages are authentic.
- Aspect of message authentication
- The content of the message has not been changed.
- The source of the message is authentic.
- The message has not been delayed and replayed.
- Techniques:
- Using conventional message encryption.
- Without message encryption.
- Message Authentication Code
- A and B have a same secret key K.
- A would send a message to B, then calculate a MAC(K, M) using secret key.
- A Send message and MAC to B
-
One way Hash Functions Hash Function don’t use secret key
- Requirements:
- H can be applied to a block of data of any size.
- H has fixed-length output.
- H is easy to compute for any given message.
- For any value h is very difficult to compute x.
- For any given x, it is very difficult to find y, such that H(x) = H(y)
- It is very difficult to find any pair (x,y) such that H(x) = H(y);
- SHA-1
- input processed in 512-bits block.
- output a 160 bits message diest.
- Requirements:
-
Identification
- Associating an identity with a subject.
Part 4 Advanced Crypto
Homomorphic encryption
- Equation
- Operation *, Enc(encryption): Enc(a * b) = Enc(a) * Enc(b)
- Partial Homomorphic encryption: just to one operation
- Fully Homomorphic scheme:
- Multiple operation and addition.
- Allow perform arbitary computations.
- Existence is by no means obvious???
CryptDB
- To query encrypted SQL database without decrypting
- Low overhead.
Zero - knowledge proofs
-
3-colorability
- Alice hides her solution, and allows Bob to choose any pair of vertices.
- Alice reshuffles actual colours, hides modified solution, then allows Bob to open any pair of vertices again.
- Repeat Step 2 until Bob convince.
-
Requirements
- Completeness: Prover should be able to convince Verifier that he has true solution
- Soundness: It should be able to convince Verifier only in true solutions.
- Zero-knowledge(nedd): Verifier should not be able to learn anything but the Prover has a solution.
-
Inactive and Non-inactive
Features Inactive Non-inactive Inactive Need No Efficient Slow Fast Security High security Low security Scene Suitable for high security scene Suitable for high efficient scene
Secure MPC(Multi Party Computations)
- The process of Yao’s Protocol
- P1 has x, P2 has y. In which x and y are private value.
- P1 would like to use two random keys Kx and Ky calculate F(x, y), then tabulate in table T(Tx, y).
- P1 send T(Tx, y) to P2.
- P1 send random keys Kx and Ky to P2.
Part 5 Legal And Social Issues
Rapid developments computer systems, networks and give rise for
- New threats for security and privacy
- New defensive measures;
Legal
-
Restriction on Cryptography
- Cryptography and Patent system
- Cryptography and Trade secret Law
- National and International regulations of cryptography
- Digital Rights management
-
Patent system
- Early development of cryptographic protocols and systems was influenced by patent law;
- Many important techniques, including public key cryptography have been patented. including (Diffie-Hellman, RSA)
- In general, one of the results of the patent protection appeared to be reduced use of the invention.
-
Trade secret Law
- Until recently many encryption algorithms were kept as proprietary, secret and protected by the trade secret provisions;
- The idea was that one could achieve additional security for the encrypted data by keeping the encryption algorithms themselves secret;
- There are still many patented algorithms and they are protected by law
-
National and International regulations
- National
- Cryptography can be used to hide criminal activities
- Strong cryptography can make difficult, or almost impossible to conduct search warrants by legal authorities;
- International
- Strong cryptography can make impossible to decrypt correspondence by military, economical.
- National
-
Clipper chip
-
Escrowed Encryption Standard:
- A cheap tamper-proof chip,each with unique ID;
- A classified encryption algorithm;
- A back door is embedded and government has a copy of a key used in every such a chip, so when authorized, every encrypted message can be decrypted
-
Potential Problems with Clipper chip
- The potential for insider abuse;
- The creation of new vulnerabilities and targets for attack;
- The difficulties of properly authenticating requests for keys;
- The cost;
-
International agreements on Cryptograph
- Allows export of mass-market software;
- Allows export of all products that use encryption to protect intellectual property
-
Digital Rights Management
- criminalizes production and dissemination of technology for circumventing the control access for the copyrighted works
-
OECD Guidelines
-
the Organization for Economic Development and Cooperation adopted a set of privacy guidelines:
-
Collection Limitation Principle: there should be limits to the collection of personal data, and any such data should be obtained by lawful and fair means;
-
Data Quality Principle: personal data should be relevant to the purposes for which it is to be used, should be accurate, complete, and kept up to date.
-
Purpose Specification Principle: the purposes for which personal data is collected should be specified not later that at the time of data collection and the subsequent use limited to the fulfilment of those purposes;
-
Use Limitation Principle: Personal data should not be disclosed, made available, or otherwise used for purposes others that those specified in advance.
-
Security Safeguards Principle: personal data should be protected by reasonable security safeguards again such risks as loss, unauthorized access, destruction.
-
Openess Principle: there should be a general policy of openess about developments, practices and policies with respect to personal data.
-
Individual Participation Principle:
- To obtain the data from a data controller. Confirmation of whether or not the data controller has data relating to him;
- To be given reasons if a request made specified as above is denied, and to be able to challenge such denial;
- To challenge data relating to him and, if the challenge is successful to have the data erased, rectified, completed, or amended.
-
Accountability principle: a data controller should be accountable for complying with measures which give effect to the principle stated
-
Firewalls
-
The firewalls implement hardware or software solutions beased on the control of network connection between local network and other networks.
-
OSI
- Application
- Presentation
- Session
- Transport
- Network
- Data link
- Physical
-
Firewall characteristics:
- All traffic from inside to outside, and vise versa, must pass through the firewall. All access to local network is block except via firewall.
- Only authorized traffic, defined by the local security policy is allowed to pass in either direction.
-
Types of control used by firewalls
- Service control: determine what types of services can be access.
- Direction control: determines in which direction particular service request may be initiated;
- User control: determines access to a service accroding to a user.
- Behaviour control: controls how particular services are used.
-
Limitations of the firewalls
- Cannot protect againsts attacks that bypass the firewall
- Does not protect internal attacks.
- Cannot protect virus programs or files.
-
Types of firewall
-
Packet filtering route: applies a set of rules to each incoming IP packet and then forwards or discards the packet.
-
Filtering rules based on:
- Source IP address
- Destination IP address
- Source and destination transport-level address
- IP protocol fields
-
Advantages:
- Simple.
- Transparent for users.
- Very fast.
-
Disadvantages:
- Lack of upper-layer functionality
- Do not support advanced user authentication schemes
- Cannot block specific application commands
-
-
Circuit-level gateway
-
Based on specified session rules
-
It sets up two connections:
- One between itself and a TCP user on the inner host;
- One between itself and a TCP user on the outer host;
-
Once connections are established and security criteria are met , both connections are linked by the gateway;
-
Advantages:
- relatively inexpensive.
- have the advantage of hiding information about the private network they protect.
-
Disadvantages:
- do not filter individual packets.
-
-
Application-level gateway
-
They can filter packets in the application layer of the OSI model.
-
Advantages:
- They offer a high level of security.
- Application specific protection.
-
Disadvantages:
- significant impact on network performance.
- are not transparent to end users.
- require manual configuration of each client computer.
-
-
-
Firewall benefits and problems
-
Benefits
- Firewalls protect private local ares networks from hostile intrusion from the internet
- Flexibility in implementation of security policies
- Relatively inexpensive solution
-
Problems
- Possible traffic bottleneck.
- Security concentrated in one spot.
-
-
Key next-generation firewall requirements
- Identify applications, not ports.
- Identify users, not just IP addresses.
- Inspect content in real-time.
- Simplify policy management.
- Deliver multi-gigabit throughput.